What Is Digital Asset Custody and Why Security Matters

Roughly half a trillion dollars in digital assets now move through global custody platforms, with American investors playing a leading role in this rapidly evolving sector. As cryptocurrencies and blockchain instruments become mainstream, security risks and regulatory demands rise just as quickly. Understanding how digital asset custody works can empower you to make smarter decisions and safeguard your investments in a modern financial world that rewards knowledge and vigilance.
Table of Contents
- Defining Digital Asset Custody In Finance
- Types Of Digital Custody Solutions Explained
- How Custodial Platforms Protect Assets
- Regulatory And Compliance Requirements
- Risks, Liabilities, And Investor Safeguards
Key Takeaways
| Point | Details |
|---|---|
| Importance of Digital Custody | Digital asset custody is vital for securing and managing investments in the $500 billion digital markets. |
| Types of Custody Solutions | Hot wallets, cold storage, and hybrid models each serve different investment needs and risk management strategies. |
| Security Measures | Advanced encryption, multi-factor authentication, and real-time monitoring are critical for asset protection. |
| Regulatory Compliance | Adhering to KYC, AML, and securities regulations is essential for safeguarding investor interests and ensuring market integrity. |
Defining Digital Asset Custody in Finance
Digital asset custody represents a sophisticated financial infrastructure designed to securely store, manage, and protect digital assets like cryptocurrencies, tokens, and blockchain-based financial instruments. Current research from Oxford Law Blogs highlights that custodians provide a crucial cornerstone of the USD 500 billion digital asset markets, underscoring the critical role these specialized financial service providers play in modern investment ecosystems.
At its core, digital asset custody involves professional third-party services that safeguard investors’ digital holdings through advanced technological and security protocols. These services go beyond traditional asset storage, offering comprehensive management strategies that include secure wallet infrastructure, multi-signature authentication, cold storage solutions, and robust regulatory compliance mechanisms. Professional custodians essentially act as digital vaults, protecting assets against potential cyber threats, unauthorized access, and potential loss scenarios that individual investors might struggle to mitigate independently.
The fundamental components of digital asset custody typically encompass several key elements:
- Secure Storage: Utilizing advanced encryption and offline cold storage techniques
- Access Management: Implementing multi-factor authentication and strict access controls
- Regulatory Compliance: Ensuring adherence to financial regulations and investor protection standards
- Asset Tracking: Providing real-time monitoring and comprehensive transaction logs
- Risk Mitigation: Developing sophisticated security frameworks to prevent potential breaches
Pro Investment Strategy: Research and select digital asset custodians with proven track records, robust security certifications, and transparent operational practices to maximize the safety of your digital investment portfolio.
By understanding digital asset custody, investors can make more informed decisions about protecting and managing their digital wealth in an increasingly complex financial landscape.
Types of Digital Custody Solutions Explained
The digital asset custody landscape encompasses several nuanced approaches, each designed to address specific investor needs and risk management strategies. Institutional custody represents the most sophisticated tier, offering comprehensive security frameworks tailored for large-scale investors, hedge funds, and financial organizations seeking enterprise-grade protection for substantial digital asset portfolios.
Three primary digital custody models have emerged in the financial technology ecosystem:
-
Hot Wallets: Online storage solutions providing immediate transaction capabilities
- Highest liquidity and accessibility
- Suitable for active trading environments
- Higher potential security vulnerabilities
-
Cold Storage Solutions: Offline storage mechanisms completely disconnected from internet networks
- Maximum security for long-term asset preservation
- Minimal risk of unauthorized digital access
- Reduced transaction speed and convenience
-
Hybrid Custody Models: Combining online and offline storage strategies
- Balanced approach between security and accessibility
- Partial asset allocation in secure offline environments
- Dynamic risk management techniques
Each custody solution presents unique advantages and potential limitations. Institutional investors typically prefer hybrid or cold storage models due to their robust security protocols and comprehensive risk mitigation strategies. These approaches incorporate advanced encryption, multi-signature authentication, and strict access control mechanisms to protect digital assets against potential cyber threats and unauthorized transactions.
Pro Security Approach: Implement a strategic asset distribution model where high-value digital assets are stored in cold storage, while smaller, actively traded portions remain in secured hot wallets with multi-factor authentication.

Understanding these custody solutions enables investors to make informed decisions aligned with their specific risk tolerance, investment goals, and operational requirements in the dynamic digital asset marketplace.
Here is a summary of key differences among digital asset custody models:
| Custody Model | Best Use Case | Security Level | Liquidity/Access |
|---|---|---|---|
| Hot Wallet | Active trading | Lower, needs vigilance | Instant, always on |
| Cold Storage | Long-term holding | Highest, offline | Slower, manual use |
| Hybrid Custody | Balanced portfolios | Mixed, configurable | Flexible, adaptable |
How Custodial Platforms Protect Assets
Custodial platforms employ sophisticated multi-layered security strategies designed to safeguard digital assets against an increasingly complex landscape of cyber threats. Recent research exploring knowledge graphs and functional pathways reveals intricate network trust mechanisms that underpin digital asset protection, highlighting the critical intersection between technological infrastructure and robust security protocols.
Asset protection in digital custody environments encompasses several critical defensive strategies:
-
Encryption Technologies
- Advanced cryptographic algorithms
- End-to-end data protection
- Comprehensive key management systems
-
Network Security
- Firewalls and intrusion detection systems
- Continuous monitoring of network traffic
- Real-time threat identification
-
Authentication Mechanisms
- Multi-factor authentication
- Biometric verification
- Role-based access controls
Blockchain-based preservation techniques provide additional layers of security, leveraging the technology’s inherent immutability and decentralized architecture to create tamper-resistant storage environments. These approaches ensure that digital assets remain protected through cryptographic signatures, distributed ledger technologies, and sophisticated access management protocols that dramatically reduce potential vulnerability points.
Institutional custodial platforms typically integrate redundant security measures, including geographic distribution of storage infrastructure, offline cold storage solutions, and comprehensive disaster recovery frameworks. These strategies create multiple defensive barriers that protect investors’ digital assets from potential breaches, unauthorized access, and systemic risks.
Pro Security Configuration: Implement a zero-trust security model with continuous authentication, granular access controls, and regular comprehensive security audits to maintain the highest possible protection for digital assets.
By understanding and implementing these advanced protection mechanisms, investors can significantly mitigate risks and ensure the long-term security of their digital wealth in an increasingly complex technological landscape.
Regulatory and Compliance Requirements
Digital asset custody operates within a complex regulatory landscape that demands rigorous compliance frameworks to protect investor interests and maintain financial system integrity. The regulatory environment continues to evolve rapidly, requiring custodial platforms to implement comprehensive strategies that address multiple layers of legal and operational requirements.
Key regulatory compliance dimensions for digital asset custody include:
-
Know Your Customer (KYC) Protocols
- Comprehensive identity verification processes
- Detailed customer background screening
- Ongoing monitoring of transactional activities
-
Anti-Money Laundering (AML) Standards
- Transaction monitoring systems
- Suspicious activity reporting mechanisms
- Risk-based compliance frameworks
-
Securities Regulation Adherence
- Registration with financial regulatory bodies
- Transparent reporting mechanisms
- Compliance with securities trading guidelines
Institutional custodians must navigate a complex web of international and domestic regulatory requirements, which often vary significantly across different jurisdictions. This necessitates developing flexible compliance infrastructures capable of adapting to changing legal landscapes while maintaining robust security protocols and investor protection mechanisms.
The most advanced digital asset custody platforms integrate sophisticated compliance technologies that leverage artificial intelligence and machine learning to detect potential regulatory violations in real-time. These systems provide automated risk assessment, transaction screening, and comprehensive audit trails that enable proactive regulatory management.
Pro Compliance Strategy: Develop a dynamic compliance framework with continuous monitoring, regular third-party audits, and adaptive technological infrastructure that can quickly respond to emerging regulatory requirements.
By prioritizing comprehensive regulatory compliance, digital asset custodians can build trust, mitigate legal risks, and create a secure environment for institutional and individual investors seeking professional asset management services.
Risks, Liabilities, and Investor Safeguards
Digital asset custody involves navigating a complex landscape of potential risks that demand sophisticated mitigation strategies. Recent cybersecurity research provides a comprehensive framework for understanding and managing the intricate cyber risks within the digital asset ecosystem, highlighting the critical need for proactive risk management approaches.
The primary risk categories for digital asset investors include:
-
Technological Risks
- Blockchain network vulnerabilities
- Smart contract potential exploits
- Infrastructure security breaches
-
Financial Risks
- Market volatility exposure
- Liquidity constraints
- Potential asset value depreciation
-
Operational Risks
- Custodial platform failures
- Authentication system compromises
- Data management inconsistencies
Investor safeguards represent a multi-layered defense mechanism designed to protect digital assets from potential threats. These protective strategies typically incorporate comprehensive insurance coverage, redundant security protocols, and advanced technological monitoring systems that continuously assess and mitigate potential vulnerabilities.
Professional custodial platforms implement rigorous risk management frameworks that go beyond traditional security measures. These include real-time threat detection algorithms, comprehensive asset tracking mechanisms, and sophisticated financial modeling techniques that anticipate and neutralize potential systemic risks before they can impact investor portfolios.
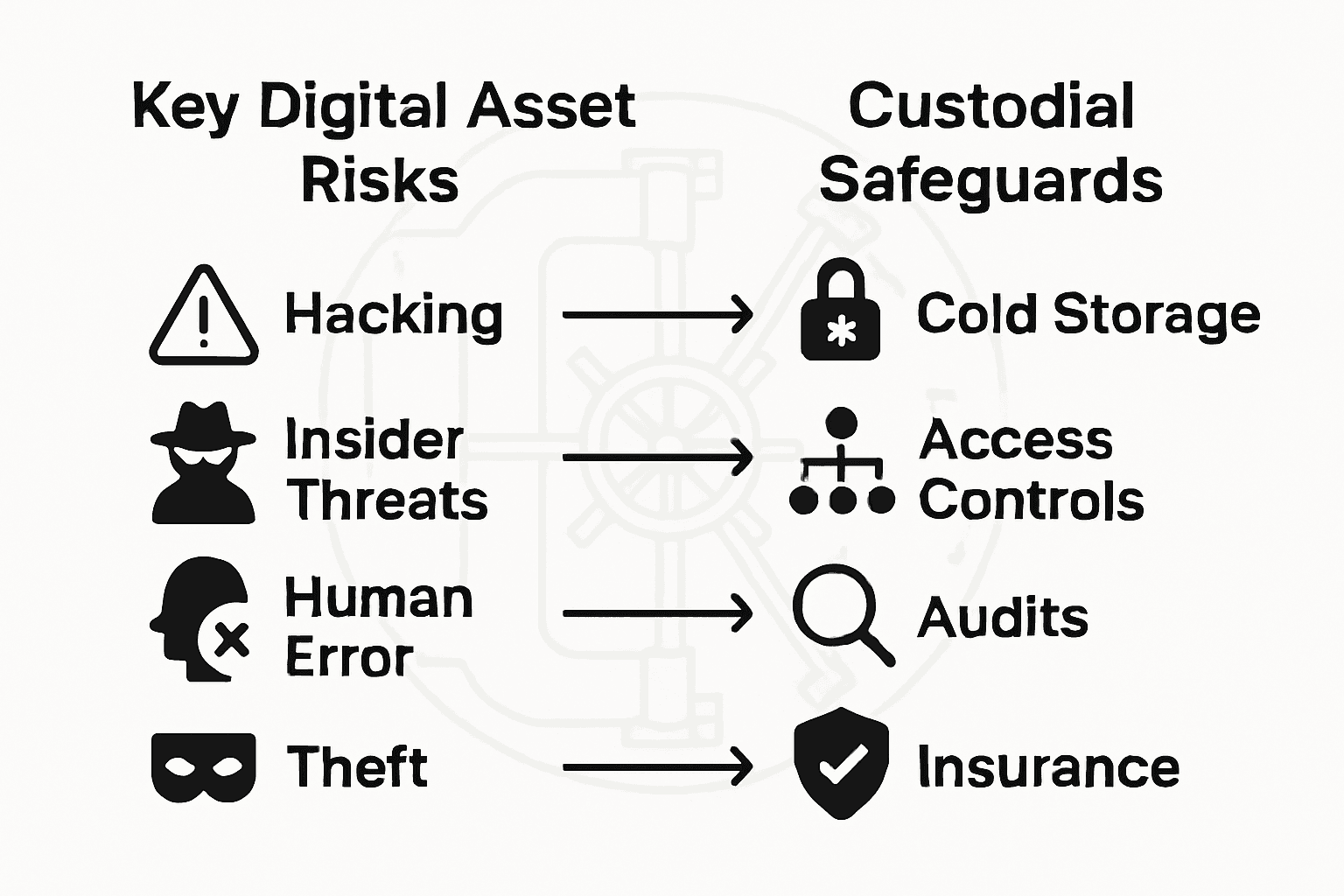
Pro Risk Mitigation Strategy: Diversify your digital asset holdings across multiple custody platforms, maintain comprehensive documentation of all transactions, and regularly conduct independent security audits to identify potential vulnerabilities in your investment strategy.
By understanding and proactively addressing potential risks, investors can create a robust defensive infrastructure that protects their digital wealth while maintaining the flexibility required in the dynamic digital asset marketplace.
Below is a comparison of critical risks and how professional custodians address them:
| Risk Type | Potential Threat | Custodial Safeguard |
|---|---|---|
| Technological | System breach, code flaws | Frequent security updates |
| Financial | Market crash, illiquidity | Asset insurance, risk modeling |
| Operational | Human error, process lapse | Multi-layer process controls |
Secure Your Digital Wealth with Trusted Asset-Backed Custody
The article highlights the critical challenge of protecting digital assets from cyber threats, unauthorized access, and complex regulatory demands. Investors like you seek transparent, compliant, and secure custody solutions that safeguard your portfolio while offering real-time insights and peace of mind. Terms such as multi-factor authentication, cold storage, and proof of reserve emphasize the need for robust security combined with verifiable asset backing.
At UK Financial Ltd, we address these concerns head-on by providing a comprehensive platform for investing in gold-backed digital assets and cryptocurrency tokens. Our flagship Maya Preferred PRA token and other asset-backed tokens are secured by verified precious metal reserves with a focus on regulatory compliance and blockchain transparency. With features like live token performance data, proof of reserve reports, and real-time blockchain tracking, you gain unmatched confidence in your investments.
Invest smartly by entrusting your digital wealth to custodial solutions designed with the highest security standards and asset integrity. Explore our full range of offerings at UK Financial Ltd today and see how you can combine innovative financial products with powerful security measures.
Protect your portfolio with the assurance of gold-backed security. Visit UK Financial Ltd now to start securing your digital assets with the reliability you deserve.
Frequently Asked Questions
What is digital asset custody?
Digital asset custody refers to specialized financial services that securely store, manage, and protect digital assets such as cryptocurrencies and tokens using advanced security measures.
Why is security important in digital asset custody?
Security is critical in digital asset custody because these assets are susceptible to cyber threats, unauthorized access, and potential loss. Professional custodians use sophisticated security protocols to safeguard these assets and ensure investor protection.
What are the different types of digital asset custody solutions?
The primary types of digital asset custody solutions include hot wallets for active trading, cold storage for long-term security, and hybrid models that combine both for a balanced approach to risk and accessibility.
How do custodial platforms protect digital assets?
Custodial platforms employ multi-layered security strategies, including encryption technologies, network security measures, and robust authentication mechanisms to protect digital assets from cyber threats and unauthorized access.
Recommended
- UK Financial Ltd – Gold-Backed Cryptocurrency Portfolio
- News | UK Financial Ltd
- UK Financial Ltd Confirms Official Corporate Structure of the Maya Preferred Project and Its Dual-Class Token System
- UK Financial Ltd Sets Official 30-Day Conversion Deadline for Three Exchange-Listed Tokens Ahead of Regulated Upgrade
- Crypto Trading Bot Security: Protecting Profits and Data