Digital Asset Security Explained: Protecting Real Value

Most american digital asset breaches trace back to overlooked fundamentals rather than exotic attack methods. For institutional investors and fund managers in the United Kingdom, the stakes have never been higher as digital assets promise both opportunity and risk. This article dispels myths about blockchain security, clarifies core protection strategies, and reveals best practices for navigating regulatory demands in the rapidly evolving digital finance sector.
Table of Contents
- Digital Asset Security Fundamentals and Myths
- Types of Digital Assets and Security Measures
- Core Components of Secure Asset Management
- Regulatory Compliance for Asset-Backed Tokens
- Risks, Investor Roles, and Best Practices
Key Takeaways
| Point | Details |
|---|---|
| Holistic Security Approach | Digital asset security requires a comprehensive strategy combining technology, compliance, and proactive risk management. |
| Regulatory Compliance | Institutional investors must adapt to evolving global regulations, ensuring continuous compliance with KYC and AML standards. |
| Asset-Specific Protocols | Different digital asset types necessitate tailored security protocols to address their unique vulnerabilities and challenges. |
| Active Investor Engagement | Investors play a crucial role in security by implementing best practices and maintaining active oversight of digital asset management. |
Digital Asset Security Fundamentals and Myths
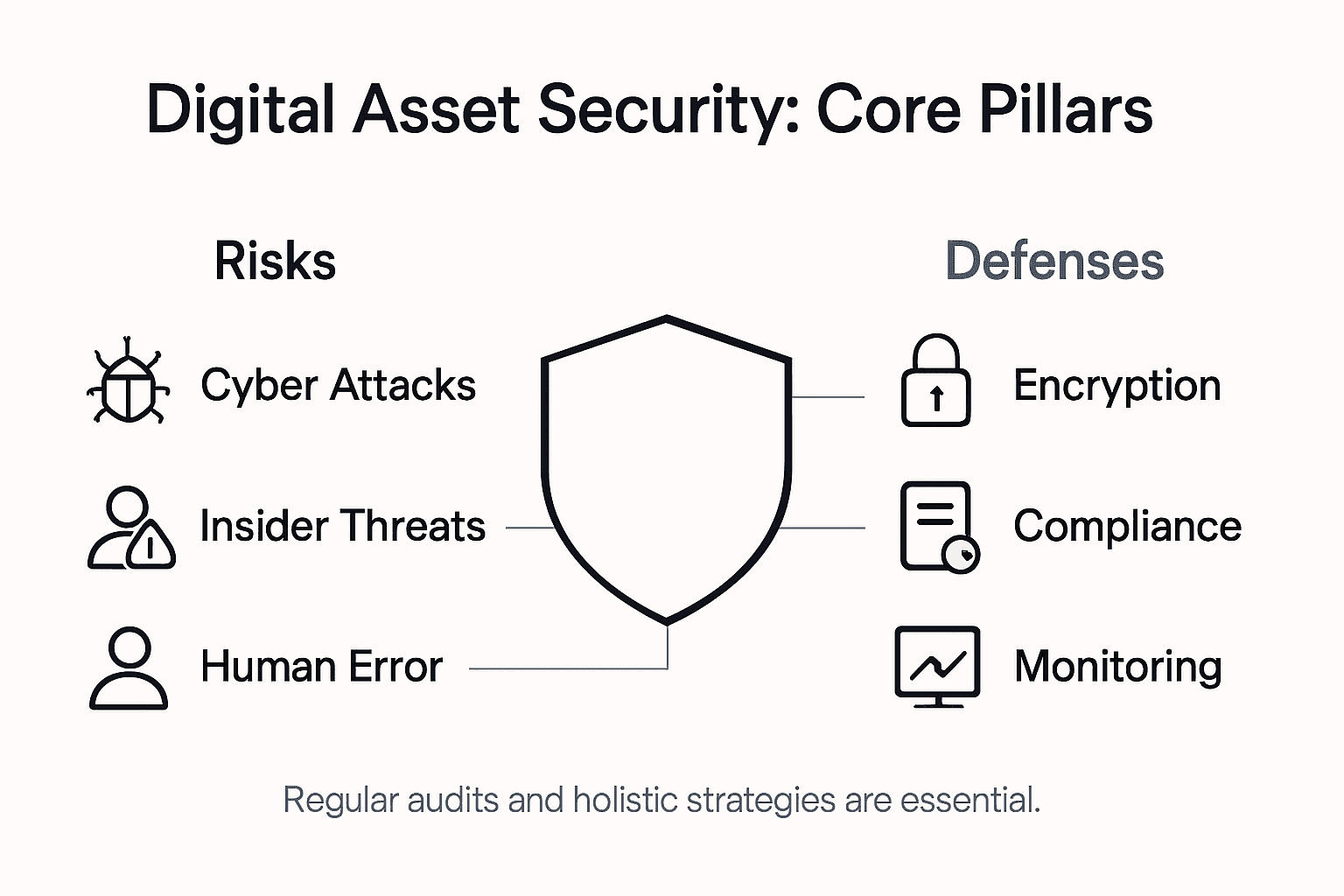
Digital asset security represents a complex landscape of technological protection and strategic risk management for institutional investors. Understanding the fundamental challenges of digital infrastructure security requires moving beyond simplistic assumptions and recognizing the nuanced threats facing modern financial technologies.
The core myth surrounding digital assets is that blockchain technology inherently guarantees complete security. In reality, security involves multiple layers of technological, operational, and regulatory safeguards. Institutional investors must recognize that while blockchain provides robust transaction recording, it does not automatically protect against all potential vulnerabilities. Cryptographic protocols can be compromised through sophisticated attack vectors including social engineering, endpoint vulnerabilities, and complex network infiltrations.
Global regulatory frameworks are increasingly emphasizing the need for comprehensive digital asset protection strategies. These emerging standards highlight several critical security considerations:
- Robust identity verification protocols
- Multi-factor authentication mechanisms
- Regular security infrastructure audits
- Comprehensive encryption strategies
- Continuous monitoring of potential threat landscapes
Understanding digital asset security requires a holistic approach that combines technological expertise, regulatory compliance, and proactive risk management. Investors must view security not as a static checkpoint but as a dynamic, continuously evolving ecosystem of protection and vigilance.
Pro tip: Implement a quarterly comprehensive security assessment that includes penetration testing, threat modeling, and review of access control mechanisms to maintain robust digital asset protection.
Types of Digital Assets and Security Measures
Digital assets represent a diverse ecosystem of financial instruments with unique security requirements and regulatory challenges. The legal classification and security frameworks for digital assets vary significantly across global jurisdictions, demanding sophisticated and nuanced protection strategies for institutional investors.
The primary categories of digital assets include cryptocurrencies, stablecoins, non-fungible tokens (NFTs), and tokenized real-world assets. Each asset type requires specialized security protocols:
- Cryptocurrencies: Demand robust cryptographic protection and cold storage mechanisms
- Stablecoins: Require rigorous reserve verification and transaction monitoring
- NFTs: Need enhanced ownership verification and provenance tracking
- Tokenized Assets: Necessitate comprehensive legal and technological authentication
Regulatory frameworks are increasingly emphasizing comprehensive security measures for different digital asset classes. These emerging standards mandate sophisticated approaches such as:
- Advanced Know Your Customer (KYC) protocols
- Anti-Money Laundering (AML) compliance mechanisms
- Decentralized identity verification systems
- Real-time transaction monitoring
- Multi-signature authentication processes
Institutional investors must recognize that security is not a one-size-fits-all solution but a dynamic, adaptive strategy tailored to specific asset characteristics and risk profiles. Continuous evaluation, technological adaptation, and proactive risk management are essential for maintaining robust digital asset protection.
Here’s a comparison of major digital asset types and their unique security challenges:
| Asset Type | Primary Vulnerability | Critical Protection Focus |
|---|---|---|
| Cryptocurrencies | Private key theft | Offline storage solutions |
| Stablecoins | Reserve mismanagement | Transparent audit processes |
| NFTs | Ownership fraud | Provenance verification |
| Tokenized Assets | Legal classification changes | Legal-compliant management |
Pro tip: Develop a comprehensive digital asset security matrix that maps specific security protocols to each asset type, enabling targeted and adaptive protection strategies.
Core Components of Secure Asset Management
Comprehensive asset security represents a multifaceted approach to protecting organizational resources and digital infrastructure, requiring systematic identification, classification, and continuous monitoring of both tangible and intangible assets. Institutional investors must develop robust frameworks that transcend traditional security paradigms and embrace holistic risk management strategies.
The fundamental components of secure asset management encompass several critical domains:
- Asset Identification: Comprehensive inventory and classification of all digital and physical resources
- Ownership Tracking: Clear documentation of asset ownership and custodial responsibilities
- Risk Assessment: Systematic evaluation of potential vulnerabilities and threat landscapes
- Access Control: Implementing granular permissions and authentication mechanisms
- Lifecycle Management: Monitoring assets from acquisition through retirement
National cybersecurity guidelines emphasize the critical importance of maintaining up-to-date asset registers as the foundation of effective security management. These registers must dynamically capture:
- Current asset locations
- Ownership details
- Operational criticality
- Interconnection dependencies
- Potential risk exposure
Successful asset management requires a proactive, adaptive approach that integrates technological solutions with strategic governance. Institutional investors must view asset security as a continuous process of assessment, refinement, and technological evolution, rather than a static compliance checklist.

Pro tip: Implement a quarterly comprehensive asset audit that includes automated discovery tools, manual verification, and cross-referencing of digital and physical asset inventories to ensure complete and accurate tracking.
Regulatory Compliance for Asset-Backed Tokens
Regulatory frameworks for asset-backed tokens represent a complex landscape of legal requirements designed to protect institutional and retail investors, demanding rigorous compliance mechanisms and transparent operational protocols. The evolving regulatory environment requires comprehensive understanding of multiple jurisdictional standards and proactive risk management strategies.
Key regulatory compliance requirements for asset-backed tokens encompass several critical dimensions:
- Know Your Customer (KYC) Protocols: Comprehensive identity verification processes
- Anti-Money Laundering (AML) Standards: Systematic transaction monitoring and reporting
- Disclosure Requirements: Transparent reporting of asset backing and reserve mechanisms
- Investor Protection Mechanisms: Defined redemption and transfer protocols
- Ongoing Compliance Auditing: Regular third-party verification of token characteristics
- Clear authorization processes
- Mandatory transparency reporting
- Consumer protection frameworks
- Standardized risk disclosure requirements
- Comprehensive supervisory mechanisms
Institutional investors must recognize regulatory compliance as a dynamic process requiring continuous adaptation. Successful navigation of this complex landscape demands sophisticated legal expertise, technological infrastructure, and a commitment to maintaining the highest standards of financial transparency and investor protection.
Pro tip: Develop a dedicated compliance task force with cross-functional expertise in legal, technological, and financial domains to ensure comprehensive regulatory adherence and proactive risk management.
Risks, Investor Roles, and Best Practices
Comprehensive risk management in digital asset investments requires a multifaceted approach that balances technological sophistication with strategic investor oversight, demanding nuanced understanding of potential vulnerabilities and proactive mitigation strategies. Institutional investors must develop robust frameworks that anticipate and neutralize complex risk landscapes.
Key risk categories for digital asset investments include:
- Technological Risks: Blockchain infrastructure vulnerabilities
- Regulatory Risks: Evolving compliance requirements
- Market Risks: Price volatility and liquidity challenges
- Operational Risks: Security infrastructure weaknesses
- Counterparty Risks: Potential systemic failures in transaction networks
Essential cybersecurity best practices form the foundation of effective digital asset protection, encompassing critical investor responsibilities:
- Implementing multi-factor authentication
- Utilizing hardware wallet solutions
- Maintaining rigorous encryption protocols
- Conducting regular security audits
- Developing comprehensive incident response strategies
Investor roles extend beyond passive investment, requiring active engagement in risk management, continuous education, and proactive security implementation. Success demands a holistic approach that integrates technological expertise, regulatory awareness, and strategic risk assessment.
The following table summarizes investor roles versus essential best practices for digital asset security:
| Investor Role | Key Responsibility | Security Impact |
|---|---|---|
| Asset Custodian | Secure asset management | Reduces unauthorized access risk |
| Compliance Manager | Regulatory oversight | Ensures legal operation |
| IT/Security Specialist | Infrastructure protection | Minimizes cyber attack exposure |
| Risk Analyst | Vulnerability assessment | Anticipates emerging threats |
Pro tip: Establish a quarterly risk assessment protocol that includes independent security audits, threat modeling, and comprehensive review of your digital asset security infrastructure.
Secure Your Digital Wealth with Asset-Backed Tokens
The article highlights the complex challenges institutional investors face when protecting digital assets including risks from cyber attacks, regulatory compliance, and the importance of multi-layered security strategies. If you are seeking true transparency, regulatory adherence, and robust security for your digital investments then exploring asset-backed tokens secured by tangible precious metals offers an exceptional solution. UK Financial Ltd specializes in digital asset security by backing cryptocurrency tokens like Maya Preferred PRA and MayaCat meme coin with verified gold and silver reserves, giving you confidence beyond blockchain recordings or theoretical protections.
Discover real-time blockchain tracking, proof of reserve reports, and live token performance data when you invest with UK Financial Ltd. These features address key pain points such as verifying asset ownership, mitigating custody risks, and navigating complex regulatory environments. Take control of your digital asset management with a platform that combines cutting-edge technology, transparent governance, and ongoing SEC compliance plans.
Explore our Gold-Backed Token Portfolio today to start securing your digital wealth with real value and regulated protection.
Leverage the strength of asset-backed digital tokens and protect your investments with confidence. Visit UK Financial Ltd now to learn how our innovative platform safeguards your digital assets while offering unmatched transparency and compliance.
Frequently Asked Questions
What is digital asset security?
Digital asset security involves the protection of financial instruments and digital infrastructure against various risks, including technological vulnerabilities, regulatory compliance issues, and operational weaknesses.
How does blockchain technology contribute to digital asset security?
While blockchain technology provides a robust framework for transaction recording, it does not guarantee complete security. Multiple layers of protection, such as cryptographic measures and regulatory safeguards, are essential to ensure comprehensive security.
What are the main types of digital assets and their security needs?
The main types of digital assets include cryptocurrencies, stablecoins, non-fungible tokens (NFTs), and tokenized real-world assets, each requiring specific security protocols like cryptographic protection, ownership verification, and legal authentication.
Why is regulatory compliance important for digital asset security?
Regulatory compliance is vital as it ensures adherence to legal standards that protect both institutional and retail investors. This includes implementing KYC protocols, AML measures, and maintaining transparent operations to mitigate risks.
Recommended
- UK Financial Ltd – Gold-Backed Cryptocurrency Portfolio
- UK Financial Ltd Sets Official 30-Day Conversion Deadline for Three Exchange-Listed Tokens Ahead of Regulated Upgrade
- UK Financial Ltd Confirms Official Corporate Structure of the Maya Preferred Project and Its Dual-Class Token System
- Official News | UK Financial Ltd
- Top Security Best Practices for Managed Email Platforms – Atriomail
- High-Security Cylinders: Everything You Need to Know – A To Z Locksmith Inc